Introduction
Welcome to the File Napper Network Tutorial. This web page explains how File Napper and it's proxy server, I-Hub, work. But before I explain how this software works, there are some other things I will need to explain to you if you don’t know them already.
IP Addresses
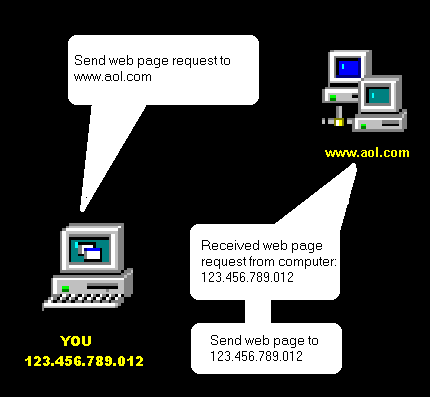
What is an IP address? It is four groups of numbers separated by a period that identifies you, from everyone else on the Internet. An example of an IP address is 123.213.231.131 In the demonstration below, a Internet user wants to download an AOL web page

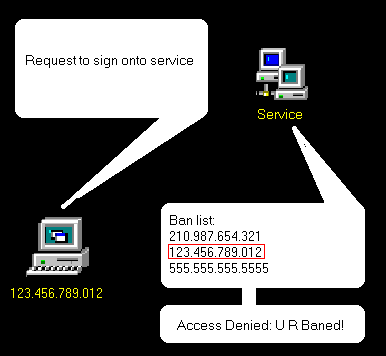
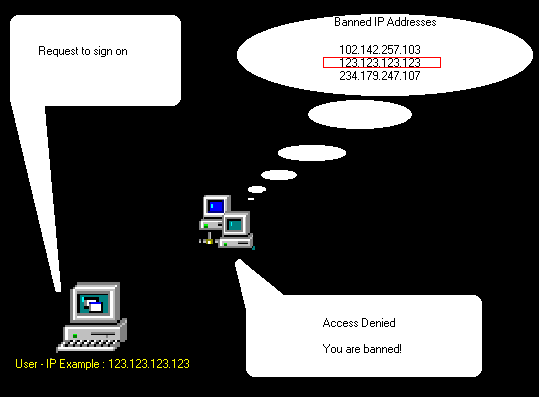
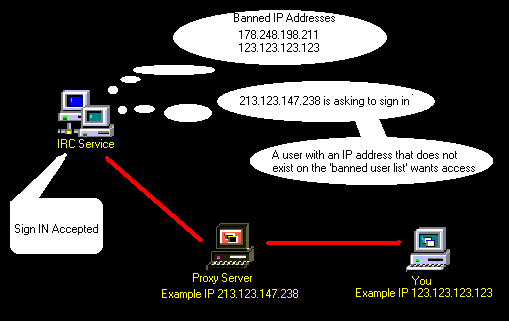
IP addresses also performs another level of identification, as Internet activity can be logged and associated with you IP address. Some public Internet services may kick out or ban a user. They usually log the IP address. Therefor creating a database of IP addresses that were banned. So every time some one asks to sign onto the service, their IP address is compared with the database. If a match is made, it means that that person was banned, and the service then has the knowledge to ignore that user. This example is show in the below image.
IRC
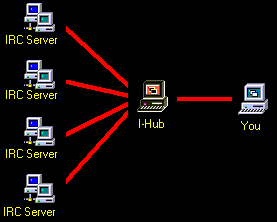
IRC (Internet Relay Chat) is a protocol that is commonly used. Most likely, you used it already weather you realized it or not. One reason it is so popular is because it is so easy to use. Anyone can search for IRC server software, and download it for free. Basically, someone needs to have the IRC server software installed, and running. Anyone who wants to join into the chatting, can just connect directly to the IP address( xxx.xxx.xxx.xxx) or Domain name (http:\\www.???.???) of the IRC server. The below example shows four users chatting. (The red lines represent the connection to the server)
File sharing & how they usually work
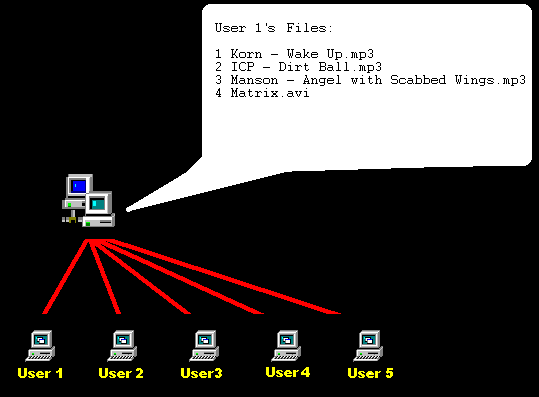
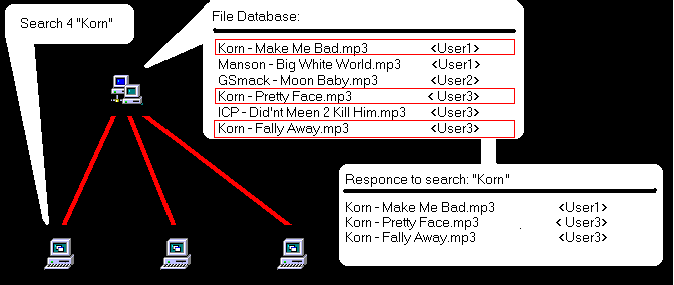
Ever since Napster has been put out by the supreme court, people from all over the world have been creating copy-cat programs that act just like it. The truth is there are hundreds, of copy-cat programs of Napster. Most of the popular ones, though may uses different protocols, usually connect to a server for searching options. Once connecting to this unknown server, you application then uploads the list of files you are sharing. Thus creating a database of files. The demonstration shows that user-1 has uploaded his 4 files to the server
The below illustration shows a user searching 4 music by "Korn"
The weakness of this strategy
If the server was to every be disconnected everyone using it will not longer have sharing capabilities. This was show with Napster, though the supreme court ruled that what it was originally doing was wrong, it still continued, but with a filter. Any one who used Napster after the installation of the filter can see how it effected the service.
Going back to IRC
The reason you may have needed to know the information above was because, sometime the connections from the computer to server, in the file sharing illustration, (the red lines) may be using a protocol similar to IRC. However, the IRC server is not as simple as you think. The IRC server works off a series of commands. Once connected to the IRC server, you can type /help to view a list of command compliant with that server. But almost every IRC server is knowledgeable of the /Join command. The /Join command is used to join a chat room. For example, if I wanted to join a chat room called "Hello" then I would type "/Join Hello". Another common command is the /Nick command, this command is used for changing you screen name on that server. If I wanted to change my screen name to "CoolDude" then I would type "/Nick CoolDude". There are many many command on an IRC server, and some, even have extra commands, programmed to by the administrator.
Another cool thing about IRC is that not all the users are may be a person. Some of them are actually software that signed onto the server. Most of the software is made for advertising. This is a common feature. They also can be very interactive. For example, this software/user may instant message you, saying that you can type a name of a file on a list it gives to you, and it may transfer you that file. Or, another example, may be trivia questions. It could give you a question, and then expect a response selecting an answer from a multiple-choice list. The below image shows a software/user sending advertisements. These circled messages were fired into the chat room over and over agin, in a given amount of time.
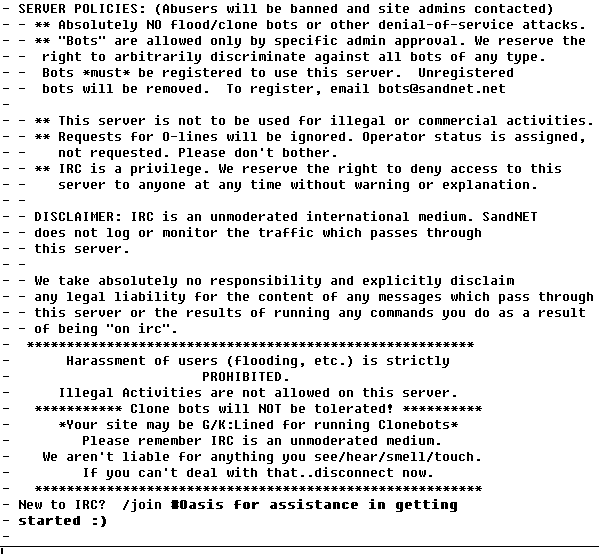
But keep in mind that most IRC servers have rules. Once you sign onto a public IRC server, then a very large message usually comes zooming by explain connection information, and the rules of the server. One of the most common rules seen is a ban on the trade of copyrighted music files, and child pornographic materiel. The below image shows the rules of irc.sandnet.net, you can usually find these rules on the IRC server’s welcome message.
As you can imagine, because of these software-users (explained in the previous paragraph), this can become a problem. As I connect to IRC The bellow image shows the first part of the irc.sandnet.net 's welcome message. NOTE: This service is obsessed with the beach, so they may replace computer names with beach items.
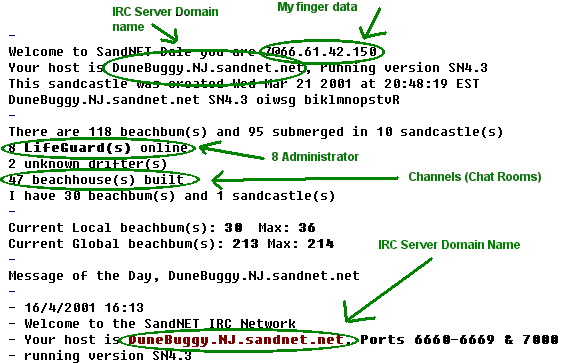
So, who's gonna catch you? Whoever setup the IRC server, or service (multiple IRC servers join as one service), usually create administrators. These administrators have the power to boot or ban a user. [You can see the administrator count on the above image]. You should recognize how a service banns a user from one of the previous chapters from above. Another scary thought is, that not only do the administrators have access to find your IP address, but every one who signs onto that server. This is accessible through the /finger command. This command pulls you IP address, your host name (user name you signed onto windows with), and you operating system. The below illustration shows a user banned from an IRC service.
File Napper
Armed with this information File Napper was built to connect to multiple public IRC Servers. There are many IRC servers out there that are operational 24/7, and proclaimed to be used by the public. File Napper accesses these chat servers and sends data to other File Napper users. All search requests would be send to all other File Napper users individually. This design of network is more efficient than the typical one, (show on section "File Sharing & how they usually work") because if you get disconnected from a single chat server, then you can depend on the other IRC server connections you are connected to. Also the chances of you getting caught is greatly decreased because it is only data which it transferred from user to user over the IRC protocol (If any one saw the text being transferred, they would not be able to read it entirely because, it is not in complete English). Plus most of the data is instant messaged. But, one important thing to remember about File Napper, is that all the users use instant messaging to communicate.

What is a Proxy Server?
And as a backup plan, there is proxy server software built especially for File Napper. Proxy servers were originally designed to give a user of a privet network, access to the Internet. This kind of proxy server may also be known as a firewall. Say if a user of a proxy server wanted to download a web page. Then the users machine would send the web page request to the proxy server, which would then be routed to the Internet. The proxy server would then download the web page and transfer that web page to the user. NOTICE!!!! As far as the Internet knows, the IP address of the proxy server was the one who downloaded the web page. This could also be used on a IRC server as well, the demonstrated below shows that the actual user (the one to the right) is banned from an IRC service. Therefor he uses the proxy server (center computer) to access the IRC server with a false IP address.
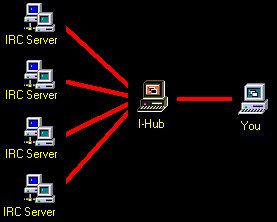
I-Hub: File Napper Proxy Server
The name of this proxy server is called I-Hub. Though the 1st version is not actually a server, it still routs IRC messages to emit a false IP address. And as you have read above (Going Back to IRC - second paragraph), this is seen as a user by the IRC server software, but is acutely a software (above we called it user-software). The I-Hub has multiple connections to multiple IRC servers, so all you need is one connection to I-Hub, to have the capability to communicate over several IRC servers.
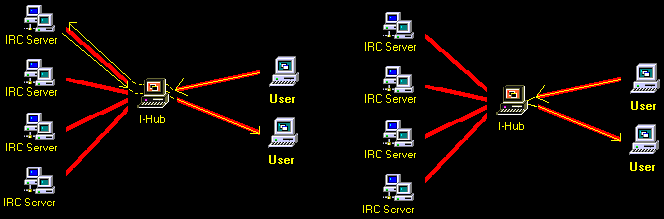
I-Hub: Smart Routing
Given the fact that most I-Hubs will be programmed to allow more than one user at a time to use it, a situation may occur where two of the users on the same I-Hub are sending messages back and forth to one another. Reading the previous sections, it would seem that the message from one user would be sent to the I-Hub, then to the IRC server. There it would pick it up and send it back only to its destination user this time. This strategy adds to Internet traffic, and takes longer. There for, the I-Hub has been programmed to recognize if a destination user is locally connected directly to itself, and routs the data to the destination user if need be. The left illustration shows the long rout, and the right shows I-Hub routing the data directly to the destination user.
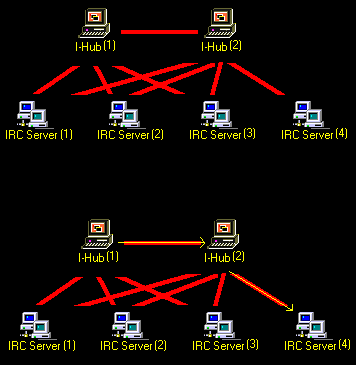
Bridged I-Hubs
However, in the unlikely event, where the IP address of an I-Hub connection was to be banned from an IRC server, then the I-Hub no longer has communication on that server its self. But don’t worry, there is a back up plan for this too. If there were multiple I-Hubs connected together acting as once service, then an I-Hub with a different IP address can connect to that IRC server, and have all the needed messages on that server routed through it. In the below illustration, I-Hub(1) is banned from IRC server(4). So in the lower image, it uses I-Hub(2) to send the message because it is not banned from IRC server(4).
FTP: Transferring the Files
Transferring of the files do not user the IRC protocol. It uses one much more known, and efficient. Instead of using a server to rout the file to a remote user, it connects directly to the user's IP address and sends the file. This is called FTP (File Transfer Protocol). File Napper uses the IRC to search other users for files, and send miscellaneous messages. And you must keep in mind that the IRC server sometimes logs you messages and IP address. But the transferring of files is not done on there service. Therefor, if a rule on the IRC service is against the trading of files, then you technically have nothing to worry about. Also, there is no service to log your FTP transfers, because the FTP connection is directly connected to the IP address of a user. The only service that could possibly log this information is you ISP (Internet Service Provider). But because of the amount of data being transferred from user to user over the Internet, it grows to be just to much to record.
The Future of File Napper
I hope to some day have a system where a software would sign onto an IRC server and I-Hub and download files of a certain type. Because this software will be signed onto the service 24/7, it can created a alternate place to download files, rather than a user who might sign off at any time, or disconnect yortransfer. If I were to create them to work together, they may also be able to share amongst each other. Also give them the ability to decide weather or not to download a file based on how many of them are out on a copied program, and the demand rate for that type of file.